Mac is not spelled S-A-F-E
- Mac OS 10.8 'Mountain Lion', however, has dropped tcpwrappers from the operating system. If you do run hunt on a server connected directly to the Internet, use firewall rules to control who can connect to the huntd server rather than hosts.allow and hosts.deny.
- Terminal is Mac OS X way into the command line world. It is designed for you to typing in specific commands that you would not be able to do otherwise. This is great for customizing your Mac and unveiling hidden features.
- This is a demo of PCE's classic Macintosh emulation, running System 6.0.8 with a bunch of games. Please be patient as you may see up to 30s of black screen upon booting, but it's worth it. If you still don't see anything, you may have to refresh the page. PCE.js Main Demo (Mac OS System 7) Follow me: @urfriendjames Contact: email protected.
Newsflash! Contrary to popular belief, if you have a Mac, you are not invulnerable to viruses and unauthorized intrusions. How shocking is that? Fact is, “Mac attacks” are happening at an increasing level of frequency, as hackers become more sophisticated and the Mac’s popularity among business users grows. (A recent survey revealed that 96 percent of enterprises now support the Mac.) Incredibly, one report found that attacks on OS X increased by 3,600 percent between 2010 and 2014. Even ransomware has joined the fray, with malware known as “KeRanger” invading the Mac world in 2016.
The Hack Mac OS X Lion to work on unsupported Core Duo & Core Solo Macs guide is free to read. We help many internet users follow up with interest in a convenient manner. The price of the Hack Mac OS X Lion to work on unsupported Core Duo & Core Solo Macs guide is free. 'If the Mac is sleeping it is still vulnerable. Just stroll up to a locked Mac, plug in the Thunderbolt device, force a reboot (ctrl+cmd+power) and wait for the password to be displayed in less than 30 seconds!' Frisk reported his findings to Apple in August and the company fixed the issues in macOS 10.12.2 released on 13 December.
There are also operating system agnostic web browser attackers, like “cross-site scripting” (XSS) and “man-in-the-browser” (MiTB). Culprits using these tools completely bypass OS X security and gain access through websites and browsers. Since so much of the work we do today is conducted through web-enabled and browser-based applications, browser attacks pose a particularly serious problem. But the take-home lesson is this: Running Mac does not exempt you from security threats. In fact, it’s getting downright scary out there.
BYOD
BYOD, or “bring your own device,” poses another significant risk. Even if you’re a Windows shop, your system can still be affected by malware written for Mac’s little brother, iOS. More and more business users are logging into corporate networks from their iPhones and iPads, so intrusions through these devices are becoming increasingly common. In late 2015, malware dubbed “XcodeGhost” was discovered on more than 50 apps available through the Apple app store. While predominantly found in China and Asia Pacific, XcodeGhost made its way into a number of domestic apps, as well. Like most other malware, XcodeGhost allows for the decryption of password information and other malicious intrusions into the victim’s system.
Macs in the Enterprise
Macs used in the enterprise are not immune, either. The new High-Sierra OS was not a day past general availability when a former NSA analyst tweeted the news of a major vulnerability. While it only took Apple about two weeks to fix it, the so-called “Keychain bug” proved that there is no system that is 100 percent secure.
Next Gen. Protection from SentinelOne
For enterprises that are heavy Mac users, a Next Gen. solution such as SentinelOne is optimal. SentinelOne offers an extremely effective protection for Mac in particular and has supported Mac High-Sierra since pre-release. Also, if ransomware bypasses SentinelOne’s agent and successfully breaches your environment you will be reimbursed up to $1 million ($1,000 per endpoint) to pay the ransom, making SentinelOne the only Next Gen. vendor to provide a financial guarantee for their product.
You can learn more about the SentinelOne Ransomware Warranty by Clicking Here.
In addition, if you want to see SentinelOne in action you can Request a Demo.
The Hack (demo) Mac Os 11
Conclusion
The Mac world, like the Windows and Linux worlds, is fraught with risk. The more popular Mac becomes in business, the more this risk increases as bad actors will put additional resources and effort into trying to crack its OS. As a Mac shop, your number one enemy is complacency. Secure your environment the best you can and do not allow yourself to be added to the list of companies that over the past year have made headlines for the wrong reasons.
It’s a commonly held belief that if you want to avoid a virus, you should be using a Mac. In fact, fewer than a dozen viruses have been developed for the Macintosh operating system. Does that mean that Mac OS is always safe and secure and, therefore, the operating system of choice? Well, not exactly.
Mac Hacks in History
In 2013, hackers exploited a flaw in Oracle Java to gain access to Apple computers. The exploit worked by gaining access via the Java Applet and provided a remote entry point to the OS X environment. Apple was quick to update the operating system to block the vulnerability, and the issue brought Apple to the forefront of the battle for third-party vendor security compliance.
In 2007, the Mac OS X firewall didn’t recognize the command to block incoming connections. This created a huge vulnerability for users because attackers could easily bypass the rule and access the Mac directly. In the same year, a flaw allowed users to bypass file- and system-level restrictions, which broke the confidentiality chain security teams value.
The year 2015 saw denial of service exploits, with over 225 vulnerabilities discovered and patched. Some of the largest were related to the integrated interface between Apple iOS, Apple Watch, Apple TV and Mac OS X. While it’s beneficial from a developer’s perspective to have a single stack for development, it causes security headaches.
Recent Vulnerabilities
The Hack (demo) Mac Os 11
More recently, a number of vulnerabilities of Mac systems have been addressed, and some haven’t. Firmware updates for the underlying computer infrastructure aren’t addressed in an efficient manner.
Third-party applications continue to be a threat vector for OS X as well. Java is such a prevalent technology that, in 2017 alone, there were over 800 reported vulnerabilities. Adobe, with it’s Flash plugin and PDF software, is also sitting with 257 known vulnerabilities in 2017, down 50 percent from the year before. But it continues to be an issue.
Apple itself continues to identify and patch vulnerabilities. The biggest ones so far have been related to Mac OS X High Sierra and a vulnerability in the keychain where an attacker could decrypt the keychain and see the keys in plain text. Also, some kernel-related flaws allowed denial of service attacks against the Apple infrastructure.
How To Stay Safe
The Hack (demo) Mac Os 13
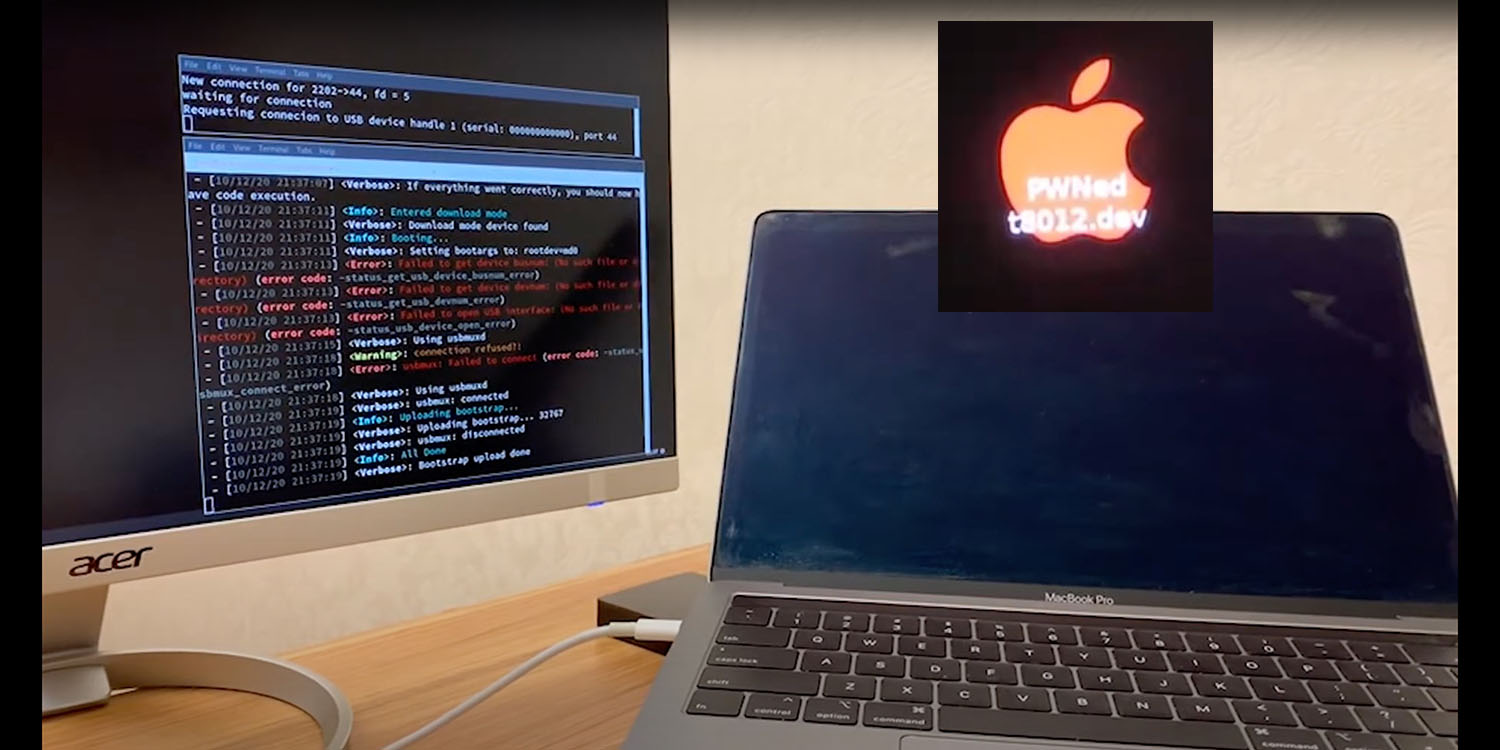
Thus far, Apple has been very focused on addressing known vulnerabilities and releasing patches for them. So, as an end user, you need to ensure that your updates are run on a regular basis. However, it is also important to have some form of protection at the system level, preferably something real-time that is effective in stopping zero day threats and signature-less attacks.
The Hack (demo) Mac Os X
A software like SentinelOne fits this mold perfectly as it runs at the kernel level and monitors all system activity, weighing potentially malicious actions to determine whether or not a program is benign or not. This approach has proven to be extremely successful as SentinelOne customers were unaffected in 2017 despite several high profile breaches. In addition, if a breach does get through then SentinelOne has a Cyber Warranty to help mitigate the financial impact on your organization. For a security product there is nothing that better exemplifies a true defense in depth solution.